What is GitHub Domain Verification?
GitHub organization domain verification confirms your organization's identity by verifying ownership of domains. A "Verified" badge appears on the organization's profile once the domain is verified. This verification is done by adding a DNS TXT record through your domain hosting service and following GitHub's domain verification process.
GitHub Domain Verification is crucial as it confirms your organization's identity on GitHub, enhancing trust. It also helps in preventing data leaks by restricting email notifications to only the verified domains, thereby safeguarding sensitive information.
To set up domain verification on GitHub:
Go to GitHub and click your profile photo, then "Your organizations".

Beside the organization, click "Settings".
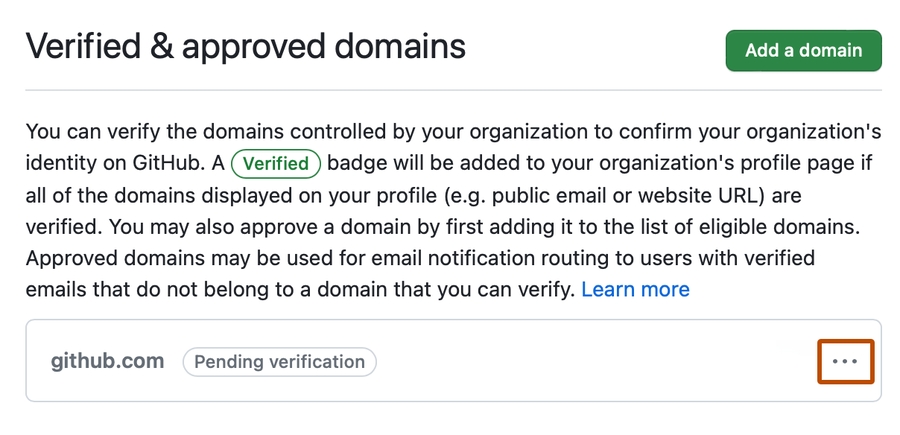
Under "Security", click "Verified and approved domains".
Click "Add a domain" and type the domain to verify, then "Add domain".
Follow the instructions to create a DNS TXT record with your domain hosting service. We recommend Cloudflare or AWS Route 53.
Wait for the DNS configuration to change, which may take up to 72 hours.
Confirm the DNS change, then navigate back to "Verified and approved domains".
Beside the domain pending verification, click the dropdown menu, then "Continue verifying" and "Verify"【9†source】.
Last updated